Using PGP/GPG encryption and decryption¶
GPG Basics¶
GnuPG encrypts messages using either a shared secret or asymmetric key pairs individually generated by GnuPG users.
Symmetric encryption¶
For implementing symmetric encryption the sending and receiving parties will share the same secret.
The secret is usually a password or pass phrase.
The shared secret must be exchanged over a secure communication channel.
Anyone holding a copy of the secret key can decrypt the data.
SFTPPlus provides support for symmetric encryption using a dedicated event handler which can automatically encrypt or decrypt files.
Asymmetric encryption¶
The key pairs used in asymmetric encryptions are composed of a public key and a private key. SFTPPlus provides support for symmetric encryption using a dedicated event handler which can automatically encrypt or decrypt files. Public keys can be exchanged with other users over insecure communication channels.
Signing other people's public keys and assigning appropriate level of trusts is the foundation on which a web of trust is built for securely exchanging signed and confidential messages.
Public keys are used for encrypting data. Private keys are used for decrypting data encrypted with the corresponding public keys.
If a partner gives you a public key, you can encrypt data with it. This data can only be decrypted by the owner of the private key associated with the public key. If that private key is lost, the encrypted data can not be recovered.
SFTPPlus provides support for asymmetric encryption using a dedicated event handler which can automatically encrypt or decrypt files from one or multiple partners.
Generating public and private key pair¶
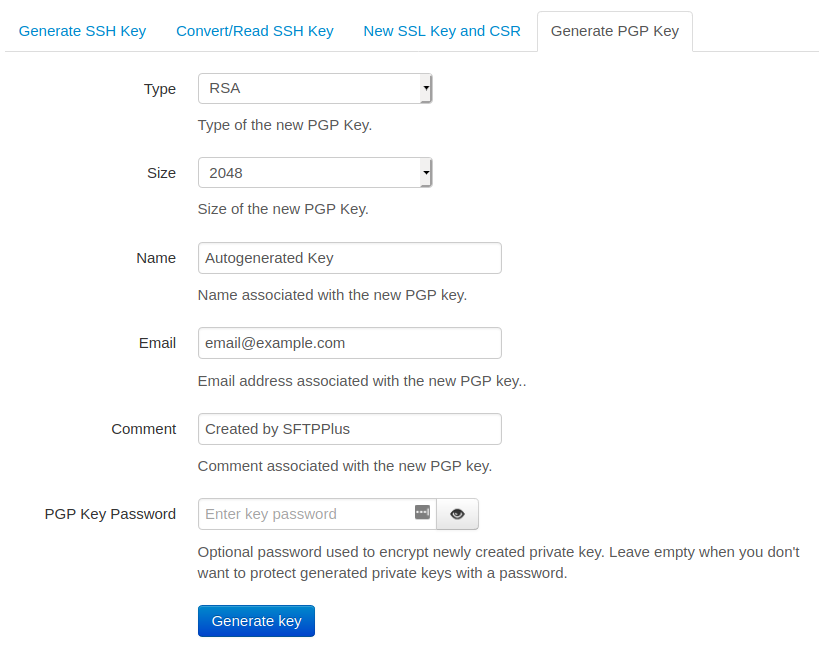
You can use the Web Manager or the embedded command line tool to create a new PGP key.
Below is a screenshot with the PGP key generation page from the Web Manager web-based administration console: