Documentation
4.2. Authentication methods¶
An authentication method configuration provides the required information to allow SFTPPlus to use a specific method in order to authenticate file transfer accounts and administration account.
You can define multiple authentication methods. You can configure the order in which these methods are used.
Consult the type configuration option to see the list of supported authentication methods.
Note
Not all authentication method types support authenticating the administrators for the Local Manager service.
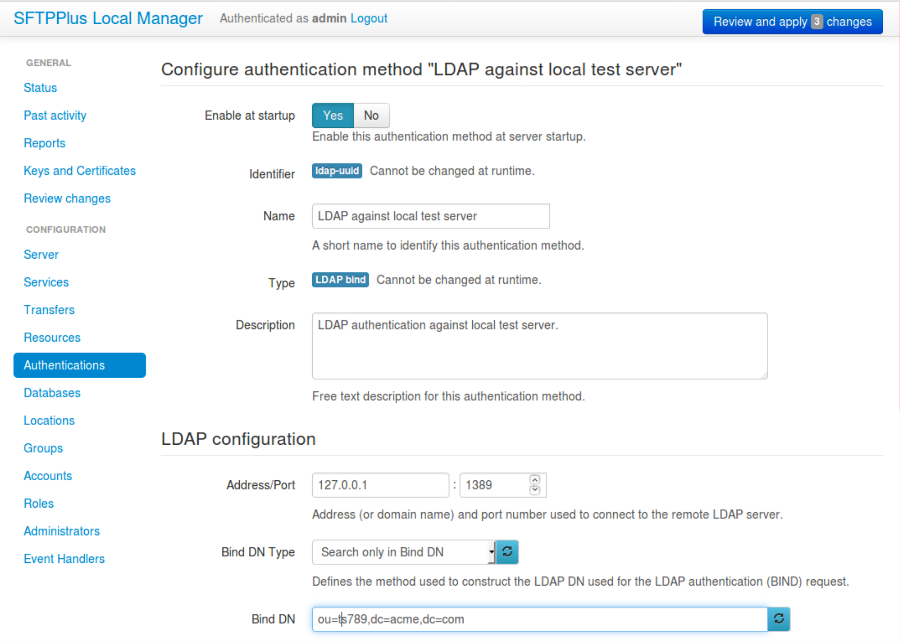
4.2.1. Adding a new authentication method via Local Manager¶
A new authentication method can be added or changed via Local Manager below. Options will differ depending on which authentication method is used.
See below for an example starting configuration for the LDAP method of authentication.
4.2.2. Adding a new authentication method via text configuration¶
Adding a new authentication method is done by creating a new section
inside the configuration file.
The name of the section should be prefixed with authentications/ and
followed by the method's UUID.
The method's UUID can be any unique string used to identify the authentication method. Once defined, the UUID should not be changed.
For more information, please see the dedicated UUID documentation.
For example, to add a new authentication method of type http
called First tier partners:
[authentications/b904ed23-a234-4ccf-8abd-edcae4d3324f]
name = First tier partners
description = Authentication based on the DUSI web application.
type = http
4.2.3. Activating an authentication method¶
Once defined, authentication methods require explicit activation by defining the ordered list of active authentication methods for the server authentication configuration option.
In this way, you can define multiple authentication methods and set their priorities. Once an account is successfully authenticated using a set method, the server will not try the remaining methods.
The following example will define a configuration in which the
authentication with UUID b904ed23-a234-4ccf-8abd-edcae4d3324f is tried
first.
If the first method cannot authenticate the account, the server
will try to authenticate it using the method with UUID ed123e-4d4724f:
[server]
name = VSP server
description = Frontend for FG partners.
authentications = b904ed23-a234-4ccf-8abd-edcae4d3324f, ed123e-4d4724f
4.2.4. Authentication method options¶
Each authentication method configuration has the following options:
4.2.4.1. name¶
- Default value
''
- Optional
Yes
- From version
2.10.0
- Values
Any text.
- Description
Human-readable short text used to identify this method.
4.2.4.2. description¶
- Default value
''
- Optional
Yes
- From version
2.10.0
- Values
Any text.
- Description
Human-readable text that describes the purpose of this authentication method.
4.2.4.3. type¶
- Default value
''
- Optional
No
- From version
2.10.0
- Values
application - Application accounts.
os - Accounts authenticated by the OS.
http - HTTP (unsecured).
ip-time-ban - Ban an IP address for a time interval.
deny-username - Deny authentication based on usernames.
anonymous - Anonymous account authentication.
ldap - Authenticate against an LDAP server.
local-file - Authenticate the accounts from a separate local file.
- Description
This option specifies the type of the method. Each type has a set of specific configuration options
4.2.5. Application-level Authentication Method¶
An application authentication method can be used to authenticate users based on accounts defined in the configuration file of SFTPPlus.
It will authenticate accounts of type application.
4.2.5.1. allowed_groups¶
- Default value
Empty
- Optional
Yes
- Values
Empty
Group UUID
Comma-separated list of group UUIDs.
- From version
4.0.0
- Description
Defines a group or a list of groups with users that are allowed by this authentication method.
When this is empty, any account is accepted as long as it has valid credentials.
For an account that is a member of multiple groups, the authentication succeeds when at least one of those groups is found in the allowed_groups list.
Note
This option applies to group UUID values, not group names. This makes it possible to rename a group without having to update this configuration option.
4.2.6. OS-level Authentication Method¶
An os authentication method can be used to authenticate users based on the authentication methods provided by the operating system.
It can also be used to authenticate administrators for the Local Manager service. For this, you will need to explicitly define a group or a set of groups in the manager_allowed_groups configuration options. By default, no administrators are allowed.
Warning
On Unix-like systems, this authentication method can only be used when the SFTPPlus service is started as root.
You can overwrite some of the account's settings (e.g. home folder path), by defining an account of type os inside the configuration file.
The os authentication method will authenticate the following account types:
Windows Local Accounts on Windows systems.
Windows Active Directory Accounts, when SFTPPlus runs on a Windows system which is part of a domain.
Linux accounts with passwords defined in the
/etc/passwdfile or by the Name Service Switch library.Linux accounts with passwords defined in the
/etc/shadowfile.
On systems supporting PAM, PAM can also be used for authenticating users with username and password credentials.
On many Unix-like systems, PAM is used for enabling various authentication methods, such as LDAP, PKCS#11 smart cards, or fingerprint authentication.
When the PAM authentication request returns PAM_SUCCESS, the account is authorized. Any response other than PAM_SUCCESS will reject the account.
PAM only handles authentication. The account configuration is retrieved using the same generic OS API.
Note
The SFTPPlus' pam authentication method will only use PAM for the authentication operation. PAM is not used for managing accounts, sessions, or passwords. Please get in touch with us if you need to integrate PAM accounts and session management with SFTPPlus.
4.2.6.1. pam_usage¶
- Default value
fallback
- Optional
Yes
- Values
fallback
exclusive
Empty
- From version
3.3.0
- Description
Defines how to use PAM for for authenticating accounts using username and password credentials.
The default mode is fallback. In this mode it will first try to authenticate accounts based on the
/etc/passwdfile. If the password is set in the operating system as one of the following x, NP, *NP* or *, it will continue to authenticate with PAM.In exclusive mode, it will exclusively use PAM for username and password authentications.
Leave it empty to completely disable PAM usage.
Note
On Windows, this option is always disabled as SFTPPlus has no support for PAM on this platform.
4.2.6.2. pam_service¶
- Default value
login
- Optional
Yes
- Values
Name of a PAM service.
- From version
3.3.0
- Description
Name of the PAM service used for account authentication requests.
4.2.6.3. allowed_groups¶
- Default value
Empty
- Optional
No
- Values
Empty
OS group name
${ALL_OS_GROUPS}
Comma-separated list of OS group names.
- From version
3.35.0
- Description
Defines an operating system group or a list of OS groups with users that are allowed by this authentication method.
When this is empty, no OS account is accepted. You need to define a list of group names for which to allow access. For example, if you need to allow all users from the local system, you can typically use the default users group available on both Windows and Linux.
If you absolutely need to allow access to all OS users from all OS groups, set this to ${ALL_OS_GROUPS}. This should be the only value, and you can't mix ${ALL_OS_GROUPS} with other group names.
Note
This configuration takes operating system group names and not SFTPPlus group names.
4.2.6.4. group_association¶
- Default value
DEFAULT_GROUP
- Optional
No
- Values
GROUP-UUID
group-name
group-name-with-default
- From version
4.11.0
- Description
Defines the SFTPPlus group that is associated with authenticated users for which no explicit association is defined inside the SFTPPlus configuration.
When set with the identifier (UUID) of a SFTPPlus group, it will associate any user with that SFTPPlus group.
When set to group-name, it will associate the user with the SFTPPlus group having the same name as the operating system group of this user. If the user is a member of multiple groups, the first group defined in allowed_groups will be used. If no SFTPPlus group is found with the same name, the authentication fails.
When set to group-name-with-default, it will try to associate the user with a SFTPPlus group having the same name as the OS group. It will use the default SFTPPlus group if no SFTPPlus group is found having the same name as the OS group.
Note
When an OS account is explicitly defined inside SFTPPlus configuration the group_association is ignored and the account's groups configuration is used instead.
4.2.6.5. manager_allowed_groups¶
- Default value
Empty
- Optional
Yes
- Values
Empty
OS group name
Comma-separated list of OS group names.
- From version
3.37.0
- Description
Defines an operating system group or a list of OS groups with users that are allowed by this method to be used for the Local Manager service.
When this is empty, any administrators are denied.
Note
This configuration takes operating system group names and not SFTPPlus group names.
4.2.6.6. Windows Domain Accounts¶
When SFTPPlus is installed on a machine belonging to a Domain Controller, it can be configured to allow accounts from a Domain Controller to access the files located on the server. These accounts are authenticated using the os authentication method.
For Domain Controller accounts, there is the option for the username to be provided in the user principal name (UPN) format:
USERNAME@EXAMPLE.COM
To specify the domain, you should use UPN format, not the legacy NebBIOS names.
Note
Active Directory accounts are only available when SFTPPlus is running on a Windows operating system. If you want to allow Active Directory accounts to access an SFTPPlus instance running on Unix-like systems, please contact our support team.
4.2.7. Local File Authentication Method¶
A local-file authentication method allows defining accounts and groups in a separate configuration file.
The file uses the same format and configuration options as the main configuration file. Only accounts and groups configurations are read from this file. Any other configurations present in the file are ignored.
The accounts and groups defined for this authentication method are independent to the main SFTPPlus application. The accounts defined in the external file can only be configured with groups defined in the same external file. They can't be configured with groups from the main configuration file.
Only application accounts can be defined to be used by this authentication method.
Note
This authentication method can't be used with the Local Manager services.
The external file is automatically reloaded every 5 minutes. This means that it can take up to 5 minutes for the changes to be visible.
4.2.7.1. path¶
- Default value
''
- Optional
No
- Values
Path on the local filesystem
- From version
3.33.0
- Description
Absolute path to a file, local to the server, in which the accounts and groups configurations are stored for this authentication method.
4.2.7.2. external_management¶
- Default value
'yes'
- Optional
yes
- Values
yes
no
- From version
3.37.0
- Description
Set to yes when you want the file used to store the identities for this authentication to be managed by an external process. For example using a configuration management system. When set to yes it will automatically reload the changes every 5 minute.
Set to no when you want to use the Local Manager to manage the identities for this authentication. When set to no, changes done to the file outside of the Local Manager are ignored.
4.2.8. LDAP Authentication Method¶
The ldap authentication method can be used to authenticate application type accounts using the information provided by a remote LDAP server.
LDAP and Secure LDAP over TLS/SSL (LDAPS) protocols are supported.
Note
Only IPv4 LDAPS servers are supported. If you require IPv6 LDAPS, contact our support team. IPv6 LDAP servers are supported when configured using IPv6 address literals.
Note
LDAP StartTLS method is not yet supported. If you require it, contact our support team.
Simple BIND operation is used for authenticating an account against the LDAP server in order to validate the credentials received from a file transfer client session.
When an authentication request is made for a transfer client session, SFTPPlus will use the provided credentials (username and password) and forward them to the configured LDAP server for validation.
Note
The LDAP authentication method is a terminal method. Once the authentication chain has reached it, it will either accept or reject the credential and will not allow any other authentication to continue with validating the credentials.
Note
Only LDAP v3 is supported. If you require a different version please contact our support team.
Successfully authenticated accounts are associated to the default group, or to a specific group based on the group_mapping configuration.
4.2.8.1. address¶
- Default value
''
- Optional
No
- Values
Host name.
Fully qualified domain name resolving an IPv4 address.
IPv4 address.
IPv6 address.
- From version
3.13.0
- Description
Host name, domain name or IP address used to connect to the remote LDAP server.
4.2.8.2. port¶
- Default value
389
- Optional
Yes
- Values
Port number.
- From version
3.13.0
- Description
Port number used by the remote LDAP server to receive client connections.
4.2.8.3. secure_connection¶
- Default value
No
- Optional
Yes
- Values
Yes
No
- From version
4.11.0
- Description
When set to yes the connection to the LDAP server will be protected by a TLS security wrapper. This will enabled LDAP over TLS/SSL communication method, also called LDAPS.
Warning
Without the ssl_certificate_authority configuration, the LDAPS connect will use TLS, but the identity of the remote server will not be validated. Use ssl_certificate_authority to define the certificate authorities allowed to issue a certificate for the remote server.
4.2.8.4. bind_dn_type¶
- Default value
parent
- Optional
No
- Values
parent
relative
absolute
direct-username
- From version
3.20.0
- Description
This field defines the method utilized to construct the LDAP DN that is administered for the LDAP authentication (BIND) request.
With bind_dn_type set to parent (or the 'Username generated from Bind DN` option in the Local Manager GUI), a distinguished name applied for the bind (authentication) operation is generated using the following method:
cn=USERNAME,BIND_DN_VALUE.Under this method, there is no need for file transfer users to consider the LDAP structure when providing the username. They can authenticate based on the usual username.
For example, if bind_dn is defined as
ou=det,dc=example,dc=comand an authentication is requested for usernameJohn, the LDAP authentication (bind) operation is set for DN as:cn=John,ou=det,dc=example,dc=com.With bind_dn_type set to absolute (or 'Absolute DN' option in the Local Manager GUI), the value from bind_dn is ignored.
When set to absolute, the end users will need to specify the full DN as part of the username.
When bind_dn_type is set to relative (or 'Append to bind DN' option in the Local Manager GUI), the provided username will be used together with the value configured for bind_dn to construct the final DN administered for the LDAP authentication operation.
With bind_dn_type set to direct-username, the username provided as part of the file transfer authentication process will be directly used for the LDAP BIND operation. Once authenticated, SFTPPlus will use the username_attribute to get the full DN associated with this username in order to obtain the configuration for the authenticated account.
4.2.8.5. bind_dn¶
- Default value
''
- Optional
No
- Values
Base distinguished name.
Multiple base DNs, one per line (Since 4.16.0)
- From version
3.13.0
- Description
Base DN used to generate the distinguished name associated with the account which needs to be authenticated.
The exact way in which the bind_dn is constructed will depend on the bind_dn_type configuration.
For more details, consult the documentation for bind_dn_type.
When bind_dn_type is set to direct-username, this is used as the base DN of the Active Directory group to which access is permitted.
Multiple base DNs can be defined, one per line. This can be used for authenticating account from multiple organizations inside the same LDAP tree or for a multi-tree / forest LDAP deployment. They will be checked from top to bottom and the authentication will succeed on the first base DN in which the account is found.
This is ignored when bind_dn_type is set to absolute.
4.2.8.6. username_attribute¶
- Default value
cn
- Optional
Yes
- Values
Attribute name.
Attribute name, @FQDN.DOMAIN.COM
- From version
3.17.0
- Description
The attribute name that LDAP uses to create the DN for performing the LDAP BIND (authentication) operation.
It is also used to create the DN from which the user configuration is retrieved.
Together with bind_dn, this is used to configure the full DN used for a specific username.
As an example, if bind_dn is defined as
dc=example,dc=com, username_attribute is defined as uid, and the authentication is requested for usernameJohn, the LDAP authentication (bind) operation is set for DN as:uid=John,dc=example,dc=com.When bind_dn_type is direct-username, this attribute is used to search the LDAP directory and retrieve the DN of the authenticated account.
Note
This option is ignored when bind_dn_type has any value other than parent or direct-username.
4.2.8.7. username_suffix¶
- Default value
Empty
- Optional
Yes
- Values
Empty
@FQDN.DOMAIN.COM
- From version
4.1.0
- Description
When bind_dn_type = direct-username you can use this configuration to define a default domain that is appended to the name of each use.
In this way, the file transfer users can login with just the username, and SFTPPlus will use the full UPN for the Active Directory authentication request.
The domain name should include the @ character. For example: username_suffix = @ad.example.com.
4.2.8.8. home_folder_attribute¶
- Default value
homeDirectory
- Optional
Yes
- Values
Attribute name.
Attribute name, home path template
Empty value.
- From version
3.13.0
- Description
Name of the attribute used to retrieve the home folder path for the account which is authenticated.
When the LDAP entry associated with the authenticated account has no such attribute or the attribute's value is empty the authentication will fail.
Leave it empty to not retrieve the home folder path from the LDAP entry, but rather inherit the value from the associated group.
You can create the home folder path by combining a configurable template and the value stored in the LDAP attribute. For example to reuse the Internet Information Service (MS IIS) user path, you can use:
home_folder_attribute: msIIS-FTPDir, E:\SFTP-Files\{msIIS_FTPDir}
4.2.8.9. extension_entry_point¶
- Default value
Empty
- Optional
Yes
- Values
API extension expression.
Empty.
- From version
4.16.0
- Description
The API entry point is defined in the format LANGUAGE:DOTTED.ENTRY.POINT,
LANGUAGE is the name of the language in which the extension is written.
DOTTED.ENTRY.POINT as an expression defining the package, module, and class name which will receive the event.
Note
At this moment, the event handler API supports the development of custom handlers based on the Python programming language.
As an example, for the file
extension/auth_ldap_noop.pydefining theAuthLDAPNoopclass, the configuration will be:extension_entry_point = python:auth_ldap_noop.AuthLDAPNoop
4.2.8.10. extension_configuration¶
- Default value
Empty
- Optional
Yes
- Values
JSON
Empty
- From version
4.16.0
- Description
A JSON value which is passed to the extension.
This is ignored when extension_entry_point is not defined.
4.2.8.11. search_filter¶
- Default value
''
- Optional
Yes
- Values
LDAP search expression.
Empty value.
- From version
3.33.0
- Description
The LDAP authentication method can also filter accepted LDAP entries, based on an LDAP search filter, to restrict access to the file transfer services.
For example, if you only want to allow access to members of the group file-transfer you can use the following search filter
(memberOf=file-transfer)Leave it empty to accept any LDAP entry, regardless of its attributes.
For more information about the search filters, check the documentation of your LDAP server in order to discover the search capabilities supported by the server.
4.2.8.12. manager_search_filter¶
- Default value
''
- Optional
Yes
- Values
LDAP search expression.
Empty value.
- From version
3.37.0
- Description
LDAP filter to select the LDAP entries allowed to act as administrators for the Local Manager service.
For example, if you only want to allow access to members of the group file-transfer-admins you can use the following search filter
(memberOf=file-transfer-admins)Leave it empty to deny any LDAP entry as administrator.
4.2.8.13. group_mapping¶
- Default value
''
- Optional
Yes
- Values
Group UUID.
Comma separated LDAP attribute name, matching value, and group UUID.
Empty value.
- From version
3.34.0
- Description
The LDAP group mapping configuration can be used to augment the LDAP data without updating the actual LDAP entries.
Setting to a single group UUID will associate all the LDAP authenticated accounts to the SFTPPlus group associated with this UUID. For more details, see the dedicated LDAP group mapping documentation.
You can create complex group mapping by specifying multiple groups which are selected based on targeted LDAP values.
The matching for LDAP attribute names is case insensitive.
Leave this configuration option empty to use the default SFTPPlus group configuration.
4.2.8.14. ssl_domains¶
- Default value
Empty
- Optional
Yes
- Values
Fully qualified domain name (FQDN)
Comma separated list of fully qualified domain names
Empty
- From version
3.42.0 This configuration option defines the domain for which SFTPPlus will request certificates from the Let's Encrypt server.
The same domain can be shared by multiple services.
The domain name is handled as a case-insensitive lower case value.
You can generate a certificate with multiple domain names (Subject Alternative Name - SAN), by defining a comma-separated list of domain names. The first name from the list is used as the common name of the certificate, while the remaining names are used for the SAN extension.
For this option to be used, you need to define a lets-encrypt resource.
4.2.8.15. ssl_certificate¶
- Default value
Empty
- Optional
Yes
- Values
Absolute path on the local filesystem.
Certificate in PEM text format (Since 3.40.0).
Certificate in PKCS12 / PXF binary format (Since 4.0.0).
Empty
- From version
1.6.0
- To version
None
- Description
This can be defined as an absolute path on the local filesystem to the file containing the SSL certificate or chain of certificates used by the component.
File content should be encoded in the Privacy-Enhanced Mail (PEM) or PKCS12 / PFX formats.
File extension should be .p12 or .pfx for the file to be recognized as a PCKS-12 certificate. The password for the PCKS12 / PFX certificate should be set in the ssl_key_password configuration option.
Note
The path should not be longer than 256 characters.
You can also define the content of the certificate as text in PEM format. In this case the configuration will look as in the following example. It's important to start each line with at least one space character and keep the number of leading spaces constant:
ssl_certificate = -----BEGIN CERTIFICATE----- MIICaDCCAdGgAwIBAgIBDjANBgkqhkiG9w0BAQUFADBGMQswCQYDVQQGEwJHQjEP ... MORE CERTIFICATE DATA ... JZQaMjV9XxNTFOlNUTWswff3uE677wSVDPSuNkxo2FLRcGfPUxAQGsgL5Ts= -----END CERTIFICATE-----
When the value contains both the certificate and the key, the configuration will look as in the following example:
ssl_certificate = -----BEGIN RSA PRIVATE KEY----- MIICXgIBAAKBgQDOoZUYd8KMYbre5zZIwR+V6dO2+cCYVS46BHbRbqt7gczkoIWh ... MORE KEY DATA ... Wh+QF3UArO8r8RYv3HRcnBjrGh+yEK93wIifVNGgy63FIQ== -----END RSA PRIVATE KEY----- -----BEGIN CERTIFICATE----- MIICaDCCAdGgAwIBAgIBDjANBgkqhkiG9w0BAQUFADBGMQswCQYDVQQGEwJHQjEP ... MORE CERTIFICATE DATA ... JZQaMjV9XxNTFOlNUTWswff3uE677wSVDPSuNkxo2FLRcGfPUxAQGsgL5Ts= -----END CERTIFICATE-----
This certificate is sent to the remote peer during the SSL/TLS handshake process.
The certificate file can contain both the certificate and the private key, in which case you don't need to set the path to the private key. Only supported for PEM encoding.
The certificate file can contain the full chain of certificates. The targeted certificate should be first in the file, followed by the chained certificates. It will advertise the certificate chain in the same order as listed in the file. Only supported for PEM encoding. (Since 3.22.0)
For server-side components using TLS/SSL secure communication, this configuration option is required. If no value is defined here, the global ssl_certificate value is used.
For the client-side component using TLS/SSL, you can disable sending the certificate as part of the handshake, by leaving this configuration option empty.
4.2.8.16. ssl_key¶
- Default value
Empty
- Optional
Yes
- Values
Absolute path on the local filesystem.
Key as PEM text format (Since 3.40.0).
Empty
- From version
1.6.0
- Description
This can be defined as an absolute path on the local filesystem to the X.509 private key file used by this component.
File content should be encoded in the Privacy-Enhanced Mail (PEM) format.
Note
The path should not be longer than 256 characters.
When the value is defined as PEM text, the configuration will look as in the following example:
ssl_key = -----BEGIN RSA PRIVATE KEY----- MIICXgIBAAKBgQDOoZUYd8KMYbre5zZIwR+V6dO2+cCYVS46BHbRbqt7gczkoIWh ... MORE KEY DATA ... Wh+QF3UArO8r8RYv3HRcnBjrGh+yEK93wIifVNGgy63FIQ== -----END RSA PRIVATE KEY-----
If ssl_certificate is not defined, any value defined for this ssl_key configuration is ignored and the global ssl_key value is used.
If the value defined in ssl_certificate option already contains the private key, this option can be omitted by leaving it empty.
4.2.8.17. ssl_key_password¶
- Default value
Empty
- Optional
Yes
- Values
Password as plain text.
Empty
- From version
1.7.19
- Description
This is used to define the password of the private key, when the private X.509 key is stored as an encrypted file.
Leave it empty to not use a password for the private key file.
4.2.8.19. ssl_certificate_revocation_list¶
- Default value
Empty
- Optional
Yes
- Values
Comma separated list of CRL paths or HTTP URLs.
crl-distribution-points
${MICROSOFT_IT_CRL}
Empty
- From version
1.6.0
- Description
It defines the locations from where one or more CRLs will be loaded.
Multiple CRLs are defined as a comma separated list.
It supports local files with absolute paths, in either of the following formats:
file:///unix/absolute/test-ca.crlfile://c:\\windows\\absolute\\test-ca.crl
Retrieving the CRL over HTTP is also supported. The HTTP request is done using non-persistent HTTP/1.1 connections. The URL will look as follows:
http://example.com/some.crl
CRL distribution points (CDP) are supported by using the crl-distribution-points configuration value.
When CRL distribution points are configured, the local certificate defined at ssl_certificate needs to have the CDP extension. The CDP advertised in the local certificate is loaded at startup in order to validate the configuration.
The distribution points configuration is mutually exclusive with local file or HTTP url configurations. When the certificate revocation list is configured to use CDP, all other configured CRL location are ignored.
Warning
HTTP redirection is not yet supported for CRL URLs. You have to configure the exact URL for the CRL.
Leave it empty to disable certificate revocation checks.
The certificate revocation list can only be used when the component is configured with CA certificates stored in a single file in PEM format.
When multiple or chained CA certificates are configured the CRL is only checked for the peer's certificate and not for the CA certificate or for an intermediate CA.
Warning
CDP publishing Delta CRL are not supported.
Note
If the certificate defines multiple HTTP-based distribution points in the CDP extension, only the first HTTP URI is used. All non HTTP or the other HTTP URIs are ignored.
The CRL file should be stored in PEM or DER format.
Note
This option is ignored if ssl_certificate_authority is not enabled.
4.2.8.20. ssl_certificate_revocation_list_refresh¶
- Default value
0
- Optional
Yes
- Values
Number of seconds
0
- From version
2.8.0
- Description
This defined the number of seconds after which a configured CRL is reloaded by this component.
When set to 0, the CRL file is initially loaded at startup and then loaded again after the Next Update field advertised in the CRL.
If the Next Publish extension is present in the CRL and this option is set to 0, the CRL will be loaded again at the date and time specified in the Next Publish extension.
If the CRL does not advertise the Next Update field you will have to configure a number of seconds after which the CRL should be reloaded, otherwise you will get a configuration error.
For example, a value of 86400 means that the CRL will be re-read after one day.
For more details about the CRL reloading see the documentation for CRL reloading rules
Note
This option is ignored if
ssl_certificate_authorityis not enabled.
4.2.8.21. ssl_cipher_list¶
- Default value
secure
- Optional
Yes
- Values
List of SSL/TLS ciphers in OpenSSL format.
secure
- From version
1.7.4
- Description
This defined the list of ciphers accepted by this component while communicating over the network.
The special keyword secure contains all the algorithms that we currently consider secure.
Connections are closed if the remote peer has no common cipher in its list of configured ciphers.
When left empty, it will default to the secure configuration.
More information about the accepted values can be found at the cryptography guide
The format for this value is the same as the one used for defining the OpenSSL cipher list. More information can be found on the OpenSSL site.
4.2.8.22. ssl_allowed_methods¶
- Default value
secure
- Optional
Yes
- Values
secure
all
tlsv1.0
tlsv1.1
tlsv1.2
tlsv1.3
- From version
1.7.4
- Description
This defines the comma-separated list of SSL and TLS methods that are accepted by this component during the secure communication handshake.
Set this to secure to allow only the TLS methods that are currently considered secure. For now, this is TLS 1.2 and TLS 1.3 but this might be changed in the future. Any other configured value is ignored.
Set this to all to allow any supported SSL or TLS method. Any other configured value is ignored.
Currently, the following methods are officially supported:
tlsv1 or tlsv1.0, which is TLS 1.0.
tlsv1.1, which is TLS 1.1.
tlsv1.2, which is TLS 1.2.
tlsv1.3, which is TLS 1.3.
Note
SSLv3 is still supported, but highly discouraged, due to the SSLv3 POODLE vulnerability. In the case that you need to interact with an old SSL implementation that only supports SSLv3, it is highly recommended to force the usage of the non-CBC cipher RC4-SHA by configuring as:
[services/681f5f5d-0502-4ebb-90d5-5d5c549fac6b] ssl_cipher_list = RC4-SHA
Support for SSLv3 will be removed in future versions.
SSLv2 is no longer supported since it is not secure.
In version 2.8.0, the following new methods were added: tlsv1.0 (alias for tlsv1), tlsv1.1 and tlsv1.2
Support for tlsv1.3 was added in version 3.47.0.
Prior to version 4.17.0, this was configured as a space separated value.
4.2.9. RADIUS Authentication Method¶
The radius authentication method can be used to authenticate application type accounts by delegating the authentication to a remote RADIUS UDP server.
When an authentication request is made for a file transfer session, SFTPPlus will use the provided credentials (username and password) and forward them to the configured RADIUS server for validation.
All authentication request are made using NAS-Port = 0. Contact our support team is you need to authenticat using a different NAS port number.
For now, PAP, CHAP, MS-CHAP-V1 and MS-CHAP-V2 are supported. Contact us if you need EAP-MD5 or other authentication protocols.
Note
Only UDP transport protocol is supported. If you require TCP support, contact our support team.
Successfully authenticated accounts are associated to the default group, or to a specific group based on the group_mapping configuration.
The implementation follows the RFC 2865 standard.
It supports multiple Filter-ID attributes, but this usage is not encouraged by RFC 5080.
Warning
Only use RADIUS over internal networks. RADIUS relies on MD5 and is not FIPS compliant.
4.2.9.1. address¶
- Default value
''
- Optional
No
- Values
Host name.
Fully qualified domain name resolving an IPv4 or IPv6 address.
IPv4 address.
IPv6 address.
- From version
4.10.0
- Description
Host name, domain name or IP address used to connect to the remote RADIUS server.
4.2.9.2. port¶
- Default value
1812
- Optional
Yes
- Values
Port number.
- From version
4.10.0
- Description
Port number used by the remote RADIUS server.
4.2.9.4. authentication_type¶
- Default value
'ms-chap-v2'
- Optional
Yes
- Values
pap
chap
ms-chap-v1
ms-chap-v2
- From version
4.13.0
- Description
The authentication type to use when sending the credentials to the RADIUS server.
Use pap for Password Authentication Protocol as specified in the main RADIUS documentation. Uses MD5.
Use chap for Challenge-Handshake Authentication Protocol as specified in the main RADIUS documentation. Uses MD5.
Use ms-chap for the Microsoft version of the Challenge-Handshake Authentication Protocol as specified in RFC 2548.
Use ms-chap-v2 for the Microsoft Challenge-Handshake Authentication Protocol Version 2 as specified in RFC 2759.
Warning
The current security standards no longer consider MS-CHAP-v2 as a secure authentication method. MS-CHAP-v2 is still in used as there are many legacy products using it.
With any authentication method, only use RADIUS over secure networks.
4.2.9.5. continue_authentication¶
- Default value
No
- Optional
Yes
- Values
Yes
No
- From version
4.10.0
- Description
Whether to continue and try other authentication methods when RADIUS server has rejected the authentication request for the current user.
If the connection to the RADIUS server fails without receiving any response from the server, the authentication fails right away.
Note
This configuration is for continuing the authentication chain when the RADIUS server has rejected the access request.
See group_mapping = ${CONTINUE} for continuing the authentication chain on success.
4.2.9.6. timeout¶
- Default value
60
- Optional
Yes
- Values
Number of seconds.
- From version
4.13.0
- Description
Duration, in seconds, to wait for a response from the RADIUS server.
If a response is not received during this period, the authentication fails.
Note
If the idle_connection_timeout value of a service is lower than the RADIUS timeout, then the login attempt may fail before the RADIUS server responds.
4.2.9.7. nas_port¶
- Default value
'0'
- Optional
Yes
- Values
Integer number
- From version
4.13.0
- Description
Value of the RADIUS NAS-Port used for the access request.
For most configurations, this can be set to 0 (zero).
4.2.9.8. debug¶
- Default value
'no'
- Optional
Yes
- Values
yes
no
- From version
4.13.0
- Description
When enabled, emit low-level protocol debug messages.
4.2.9.9. group_mapping¶
- Default value
''
- Optional
Yes
- Values
Group UUID.
Comma separated RADIUS attribute name, matching value, and group UUID.
Empty value.
- From version
4.10.0
- Description
The group mapping configuration can be used to associate a successfully authenticated user with an SFTPPlus group, based on the RADIUS attributes found in the Access-Accept message.
Setting to a single group UUID will associate all the RADIUS authenticated accounts to the same SFTPPlus group.
You can create complex group mapping by specifying multiple groups which are selected based on RADIUS attribute names and values. Define group mappings, one rule per line.
The first line should always contain a single value which is the default group used in the case in which no RADIUS attribute is matched.
Subsequent lines will contain 3 comma separated values. The first value is the name of the RADIUS attribute, which is a case insensitive value. The second value is a matching expression used to match the value of the RADIUS attribute. The third value is the SFTPPlus group UUID used to associate the authenticated user to.
You can use the ${CONTINUE} value instead of the group UUID to instruct SFTPPlus to continue authenticating using the next methods from the authentication chain.
Leave this configuration option empty to use the default SFTPPlus group configuration.
4.2.10. HTTP Authentication Method¶
An http authentication method asks a remote HTTP resource to authenticate an account and provide the account's configuration.
Note
This authentication method can't be used with the Local Manager services.
To get more details about the request format and the expected result, see the dedicated HTTP authentication protocol documentation.
4.2.10.1. url¶
- Default value
''
- Optional
No
- Values
URL
Comma separated list of URLs (Since 3.51.0)
- From version
2.10.0
- Description
Full URL of a resource used to authenticate an account.
You can define a fall-back/redundant URL using a comma separates list of URLs. The first URL from the list will be used. When failing to get a response for the first URL, the remaining URLs are tried. Since 3.51.0.
4.2.10.2. timeout¶
- Default value
120
- Optional
Yes
- Values
Number of seconds.
- From version
4.13.0
- Description
Duration, in seconds, to wait for a response from the HTTP server.
If a response is not received during this period, the authentication fails.
4.2.10.3. username¶
- Default value
''
- Optional
yes
- From version
3.30.0
- Values
Text.
- Description
Username used to authenticate to the remote HTTP server.
Leave this value empty in order to leave out HTTP Basic authentication.
This will overwrite any custom Authorization header set via the headers configuration option.
Warning
For now, only HTTP Basic authentication is supported. This will send the username and password in clear text (BASE64 encoded).
4.2.10.4. password¶
- Default value
''
- Optional
Yes
- From version
3.30.0
- Values
Plain text password.
Empty.
- Description
Password associated with the configured username.
4.2.10.5. headers¶
- Default value
''
- Optional
Yes
- From version
4.4.0
- Values
Header-Name: Header-Value
Multiple headers on separate lines
- Description
This defines a set of extra headers which are sent with each HTTP request.
4.2.10.6. test_at_start¶
- Default value
'Yes'
- Optional
Yes
- From version
4.5.0
- Values
Yes
No
- Description
When set to Yes it will check at startup that the configured URL can be reached and fail to start if the URL is not available to respond to authentication requests.
4.2.10.7. proxy¶
- Default value
''
- Optional
Yes
- Values
URI like expression.
connect://12.342.421.2:3128
- From version
3.20.0
- Description
This configuration adds the proxy used to connect to the final URL.
For now, only the HTTP/1.1 CONNECT tunneling proxy method is supported.
4.2.10.8. ssl_domains¶
- Default value
Empty
- Optional
Yes
- Values
Fully qualified domain name (FQDN)
Comma separated list of fully qualified domain names
Empty
- From version
3.42.0 This configuration option defines the domain for which SFTPPlus will request certificates from the Let's Encrypt server.
The same domain can be shared by multiple services.
The domain name is handled as a case-insensitive lower case value.
You can generate a certificate with multiple domain names (Subject Alternative Name - SAN), by defining a comma-separated list of domain names. The first name from the list is used as the common name of the certificate, while the remaining names are used for the SAN extension.
For this option to be used, you need to define a lets-encrypt resource.
4.2.10.9. ssl_certificate¶
- Default value
Empty
- Optional
Yes
- Values
Absolute path on the local filesystem.
Certificate in PEM text format (Since 3.40.0).
Certificate in PKCS12 / PXF binary format (Since 4.0.0).
Empty
- From version
1.6.0
- To version
None
- Description
This can be defined as an absolute path on the local filesystem to the file containing the SSL certificate or chain of certificates used by the component.
File content should be encoded in the Privacy-Enhanced Mail (PEM) or PKCS12 / PFX formats.
File extension should be .p12 or .pfx for the file to be recognized as a PCKS-12 certificate. The password for the PCKS12 / PFX certificate should be set in the ssl_key_password configuration option.
Note
The path should not be longer than 256 characters.
You can also define the content of the certificate as text in PEM format. In this case the configuration will look as in the following example. It's important to start each line with at least one space character and keep the number of leading spaces constant:
ssl_certificate = -----BEGIN CERTIFICATE----- MIICaDCCAdGgAwIBAgIBDjANBgkqhkiG9w0BAQUFADBGMQswCQYDVQQGEwJHQjEP ... MORE CERTIFICATE DATA ... JZQaMjV9XxNTFOlNUTWswff3uE677wSVDPSuNkxo2FLRcGfPUxAQGsgL5Ts= -----END CERTIFICATE-----
When the value contains both the certificate and the key, the configuration will look as in the following example:
ssl_certificate = -----BEGIN RSA PRIVATE KEY----- MIICXgIBAAKBgQDOoZUYd8KMYbre5zZIwR+V6dO2+cCYVS46BHbRbqt7gczkoIWh ... MORE KEY DATA ... Wh+QF3UArO8r8RYv3HRcnBjrGh+yEK93wIifVNGgy63FIQ== -----END RSA PRIVATE KEY----- -----BEGIN CERTIFICATE----- MIICaDCCAdGgAwIBAgIBDjANBgkqhkiG9w0BAQUFADBGMQswCQYDVQQGEwJHQjEP ... MORE CERTIFICATE DATA ... JZQaMjV9XxNTFOlNUTWswff3uE677wSVDPSuNkxo2FLRcGfPUxAQGsgL5Ts= -----END CERTIFICATE-----
This certificate is sent to the remote peer during the SSL/TLS handshake process.
The certificate file can contain both the certificate and the private key, in which case you don't need to set the path to the private key. Only supported for PEM encoding.
The certificate file can contain the full chain of certificates. The targeted certificate should be first in the file, followed by the chained certificates. It will advertise the certificate chain in the same order as listed in the file. Only supported for PEM encoding. (Since 3.22.0)
For server-side components using TLS/SSL secure communication, this configuration option is required. If no value is defined here, the global ssl_certificate value is used.
For the client-side component using TLS/SSL, you can disable sending the certificate as part of the handshake, by leaving this configuration option empty.
4.2.10.10. ssl_key¶
- Default value
Empty
- Optional
Yes
- Values
Absolute path on the local filesystem.
Key as PEM text format (Since 3.40.0).
Empty
- From version
1.6.0
- Description
This can be defined as an absolute path on the local filesystem to the X.509 private key file used by this component.
File content should be encoded in the Privacy-Enhanced Mail (PEM) format.
Note
The path should not be longer than 256 characters.
When the value is defined as PEM text, the configuration will look as in the following example:
ssl_key = -----BEGIN RSA PRIVATE KEY----- MIICXgIBAAKBgQDOoZUYd8KMYbre5zZIwR+V6dO2+cCYVS46BHbRbqt7gczkoIWh ... MORE KEY DATA ... Wh+QF3UArO8r8RYv3HRcnBjrGh+yEK93wIifVNGgy63FIQ== -----END RSA PRIVATE KEY-----
If ssl_certificate is not defined, any value defined for this ssl_key configuration is ignored and the global ssl_key value is used.
If the value defined in ssl_certificate option already contains the private key, this option can be omitted by leaving it empty.
4.2.10.11. ssl_key_password¶
- Default value
Empty
- Optional
Yes
- Values
Password as plain text.
Empty
- From version
1.7.19
- Description
This is used to define the password of the private key, when the private X.509 key is stored as an encrypted file.
Leave it empty to not use a password for the private key file.
4.2.10.12. ssl_certificate_authority¶
- Default value
Empty
- Optional
Yes
- Values
Absolute path on the local file.
Content of the CA chain (Since 3.40.0).
${LETS_ENCRYPT_X3_CA}
${MICROSOFT_IT_CA}
${GO_DADDY_G2_G1}
Empty
- From version
1.6.0
- Description
This can be defined as an absolute path on the local filesystem to a file containing the certificates of the Certificate Authorities used to validate the remote peer.
This is used only for certificate-based peer validation. To add the CA certificate for an SSL certificate for this component, simply add it to ssl_certificate, possibly together with other certificates needed to complete the full chain of certificates.
The remote peer identity can only be validated when the remote address is configured using a fully qualified domain name. IP based validation will always fail, this is not a method accepted by the public certificate authorities.
You can define the content of the CA as text in PEM format.
When the value is defined as PEM text, the configuration will look as in the following example:
ssl_certificate_authority = -----BEGIN CERTIFICATE----- MIICaDCCAdGgAwIBAgIBDjANBgkqhkiG9w0BAQUFADBGMQswCQYDVQQGEwJHQjEP ... MORE CERTIFICATE DATA ... JZQaMjV9XxNTFOlNUTWswff3uE677wSVDPSuNkxo2FLRcGfPUxAQGsgL5Ts= -----END CERTIFICATE-----
When a certificate authority is defined, this will result in initiating the two-way SSL/TLS authentication/handshake validation. For a successful connection, make sure the remote peer sends a valid certificate. If the connection fails, the event with ID 40009 is emitted.
The certificate authority file should be stored as a file in PEM format. For multiple CA, place all certificates in the same file.
A series of bundle CA are distributed with SFTPPlus. They can be configured together and mixed with other CA certificates. The bundle CAs are available under the following names:
${LETS_ENCRYPT_X3_CA} - For Let's Encrypt X3 certificate authority.
${MICROSOFT_IT_CA} - For all Microsoft IT CA certificates, used by SharePoint Online and other services provided by Microsoft.
${GO_DADDY_G2_G1} - For all GoDaddy Certificate Bundles, G2 With Cross to G1.
To configure a component to accept the remote peer certificates signed by Microsoft IT CA, which is the CA used by SharePoint Online, you can set the configuration as:
ssl_certificate_authority = ${MICROSOFT_IT_CRL}This defines the path on the local filesystem to a file containing the certificate in PEM format for the single certificate authority or multiple authorities authorities with which this component will communicate.
Only peer connections using certificates signed by one of these certificate authorities will be permitted to communicate to this component.
When this component should communicate with peers holding certificates issued by multiple certificate authorities, put each CA certificate in PEM format inside a single file.
Leave it empty to disable checking the issuer of the peer's certificates.
When certificate authority check is disabled, connection peers are not required to send a certificate. If the peer sends a certificate, it is ignored.
4.2.10.13. ssl_certificate_revocation_list¶
- Default value
Empty
- Optional
Yes
- Values
Comma separated list of CRL paths or HTTP URLs.
crl-distribution-points
${MICROSOFT_IT_CRL}
Empty
- From version
1.6.0
- Description
It defines the locations from where one or more CRLs will be loaded.
Multiple CRLs are defined as a comma separated list.
It supports local files with absolute paths, in either of the following formats:
file:///unix/absolute/test-ca.crlfile://c:\\windows\\absolute\\test-ca.crl
Retrieving the CRL over HTTP is also supported. The HTTP request is done using non-persistent HTTP/1.1 connections. The URL will look as follows:
http://example.com/some.crl
CRL distribution points (CDP) are supported by using the crl-distribution-points configuration value.
When CRL distribution points are configured, the local certificate defined at ssl_certificate needs to have the CDP extension. The CDP advertised in the local certificate is loaded at startup in order to validate the configuration.
The distribution points configuration is mutually exclusive with local file or HTTP url configurations. When the certificate revocation list is configured to use CDP, all other configured CRL location are ignored.
Warning
HTTP redirection is not yet supported for CRL URLs. You have to configure the exact URL for the CRL.
Leave it empty to disable certificate revocation checks.
The certificate revocation list can only be used when the component is configured with CA certificates stored in a single file in PEM format.
When multiple or chained CA certificates are configured the CRL is only checked for the peer's certificate and not for the CA certificate or for an intermediate CA.
Warning
CDP publishing Delta CRL are not supported.
Note
If the certificate defines multiple HTTP-based distribution points in the CDP extension, only the first HTTP URI is used. All non HTTP or the other HTTP URIs are ignored.
The CRL file should be stored in PEM or DER format.
Note
This option is ignored if ssl_certificate_authority is not enabled.
4.2.10.14. ssl_certificate_revocation_list_refresh¶
- Default value
0
- Optional
Yes
- Values
Number of seconds
0
- From version
2.8.0
- Description
This defined the number of seconds after which a configured CRL is reloaded by this component.
When set to 0, the CRL file is initially loaded at startup and then loaded again after the Next Update field advertised in the CRL.
If the Next Publish extension is present in the CRL and this option is set to 0, the CRL will be loaded again at the date and time specified in the Next Publish extension.
If the CRL does not advertise the Next Update field you will have to configure a number of seconds after which the CRL should be reloaded, otherwise you will get a configuration error.
For example, a value of 86400 means that the CRL will be re-read after one day.
For more details about the CRL reloading see the documentation for CRL reloading rules
Note
This option is ignored if
ssl_certificate_authorityis not enabled.
4.2.10.15. ssl_cipher_list¶
- Default value
secure
- Optional
Yes
- Values
List of SSL/TLS ciphers in OpenSSL format.
secure
- From version
1.7.4
- Description
This defined the list of ciphers accepted by this component while communicating over the network.
The special keyword secure contains all the algorithms that we currently consider secure.
Connections are closed if the remote peer has no common cipher in its list of configured ciphers.
When left empty, it will default to the secure configuration.
More information about the accepted values can be found at the cryptography guide
The format for this value is the same as the one used for defining the OpenSSL cipher list. More information can be found on the OpenSSL site.
4.2.10.16. ssl_allowed_methods¶
- Default value
secure
- Optional
Yes
- Values
secure
all
tlsv1.0
tlsv1.1
tlsv1.2
tlsv1.3
- From version
1.7.4
- Description
This defines the comma-separated list of SSL and TLS methods that are accepted by this component during the secure communication handshake.
Set this to secure to allow only the TLS methods that are currently considered secure. For now, this is TLS 1.2 and TLS 1.3 but this might be changed in the future. Any other configured value is ignored.
Set this to all to allow any supported SSL or TLS method. Any other configured value is ignored.
Currently, the following methods are officially supported:
tlsv1 or tlsv1.0, which is TLS 1.0.
tlsv1.1, which is TLS 1.1.
tlsv1.2, which is TLS 1.2.
tlsv1.3, which is TLS 1.3.
Note
SSLv3 is still supported, but highly discouraged, due to the SSLv3 POODLE vulnerability. In the case that you need to interact with an old SSL implementation that only supports SSLv3, it is highly recommended to force the usage of the non-CBC cipher RC4-SHA by configuring as:
[services/681f5f5d-0502-4ebb-90d5-5d5c549fac6b] ssl_cipher_list = RC4-SHA
Support for SSLv3 will be removed in future versions.
SSLv2 is no longer supported since it is not secure.
In version 2.8.0, the following new methods were added: tlsv1.0 (alias for tlsv1), tlsv1.1 and tlsv1.2
Support for tlsv1.3 was added in version 3.47.0.
Prior to version 4.17.0, this was configured as a space separated value.
4.2.11. Deny Authentication Method¶
A deny-username authentication method can be used to block/deny authentication for a configured list of denied users.
You can use it for file transfer services, as well as for the Local Manager service.
Note
Add this authentication method as the first one in the list of active authentication methods to make sure the users are not authenticated earlier by other authentication methods.
4.2.11.1. usernames¶
- Default value
''
- Optional
Yes
- Values
Comma-separated list of usernames.
- From version
3.0.0
- Description
Comma-separated list of usernames denied by this authentication method.
The check is done in case-insensitive mode, by comparing against the lower-case name.
Usernames should be defined in lower-case.
4.2.12. Ban IP for a time interval¶
An ip-time-ban authentication method can be used to block/deny authentication requests coming from a specific IP address if they generate a number of consecutive authentication failures. This option can be used to help mitigate DDOS attempts to SFTPPlus services.
The ban is active for a time interval, after which authentication requests made from the IP address are accepted again.
When the authentication method is restarted it will reset its internal record of source IP addressed which have previously generated failed authentication requests.
When the same authentication method is used for multiple file transfer services and the Local Manager services, it will use a single internal state for each username. Multiple consecutive authentication failures for different services have the same effect as multiple consecutive authentication failures for the same service.
Note
Add this authentication method as the first one in the list of active authentication methods to make sure the users are not accepted earlier by other authentication methods.
Warning
SFTPPlus is behind a load balancer, make sure that Proxy Protocol version 2 is enabled on both the load balancer and SFTPPlus file transfer services. Otherwise all the authentication requests will be made using the load balancer own IP address and not the client IP address.
Warning
Do not use this method if SFTPPlus is behind a Proxy/Gateway or any other network device which does not preserve the source IP address of the initial authentication request or does not support Proxy Protocol v2
The ban applies to the source IP address used to initiate the authentication requests.
If SFTPPlus server is behind a Proxy/Gateway, all requests will come from the gateway's own IP address.
Check that your network is not vulnerable to IP address spoofing .
4.2.12.1. ban_interval¶
- Default value
3600
- Optional
Yes
- Values
Number of seconds.
- From version
3.2.0
- Description
Number of seconds for which authentication requests from the source IP are denied.
Default interval is 1 hour.
4.2.12.2. ban_after_count¶
- Default value
5
- Optional
Yes
- Values
Number of failed attempts.
- From version
3.2.0
- Description
Number of consecutive failed authentications which will result in blocking the source IP.
4.2.13. Anonymous Authentication Method¶
An anonymous authentication method can be used to authenticate a specific application type account by ignoring the provided password or any other credential.
This authentication is implemented based on the RFC 1635 but it can also be used for SFTP/SCP or HTTP/HTTPS services.
Once authenticated, the anonymous account will have the same permissions as the account with which it's associated. The audit events are recorded under the associated account name and not the anonymous account.
Note
This authentication method can't be used with the Local Manager service.
The anonymous account is locked inside the home folder and will have full access to all files and directories located in the home folder, just like a normal application account.
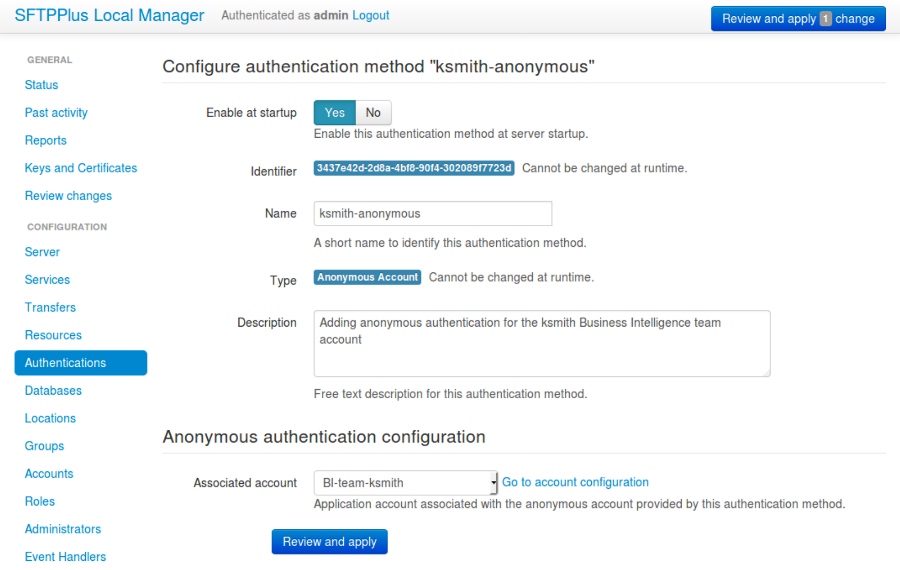
4.2.13.1. anonymous_account_uuid¶
- Default value
''
- Optional
No
- Values
UUID of the application account with which this account is associated.
- From version
3.2.0
- To version
None
- Description
This is the UUID of the application account associated with the anonymous account.